In that post, we will describe how to automate the password rotation for local accounts on Windows VM deployed on Azure.
If like me, you store passwords and SSH keys on Azure Key Vault, I bet a coin that you could be interested by the following steps 😉
As in a recipe we need ingredients, we will need services previously deployed in our subscription.
For those who wish, you will find by the following link, Terraform (TF) files allowing you to deploy these components:
- A ResourceGroup (RG)
- A VNET and a Subnet
- An Automation Account (AA) including:
- Az.Accounts Powershell module
- Az.Compute Powershell module
- Az.KeyVault Powershell module
- Variables
- A KeyVault including:
- Secret to store SPN secret
- Secret to store onag-admin password
- A Virtual Machine (VM) with the following parts:
- A Network Interace Card (NIC)
- A Public IP (PIP
- A Network Security Group (NSG)
Before going any further, a reminder on what are the two services that we are going to use in our tasks.
Azure Automation Account:
Look at a previous post (in French) which will greatly help us today.
Azure Key Vault:
On the official website, Azure Key Vault is described as:
A cloud service for securely storing and accessing secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, certificates, or cryptographic keys.
We are now up-to-date, so Ready to go forward ?!
Use case:
Infrastructure schema
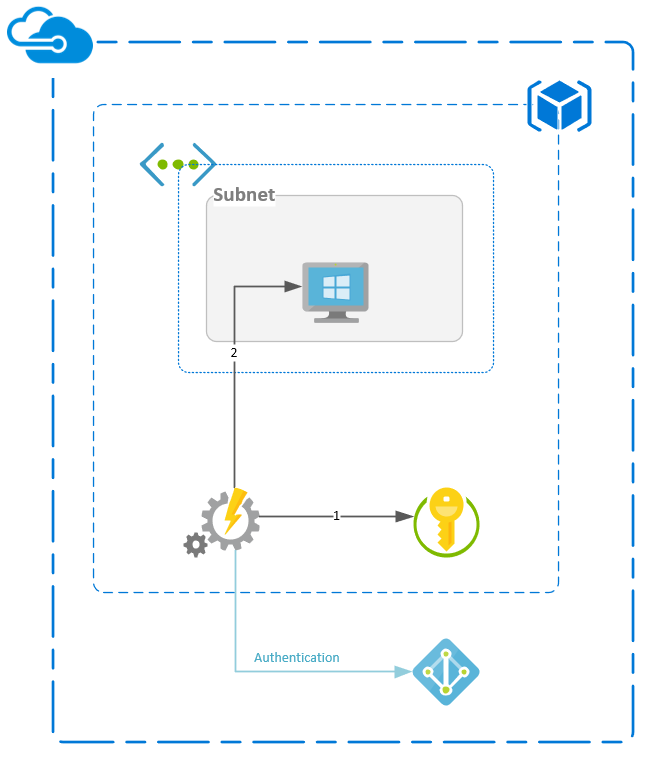
Infrastructure deployment
By deploying the TF script, or by doing it by yourself, we must have the following components:
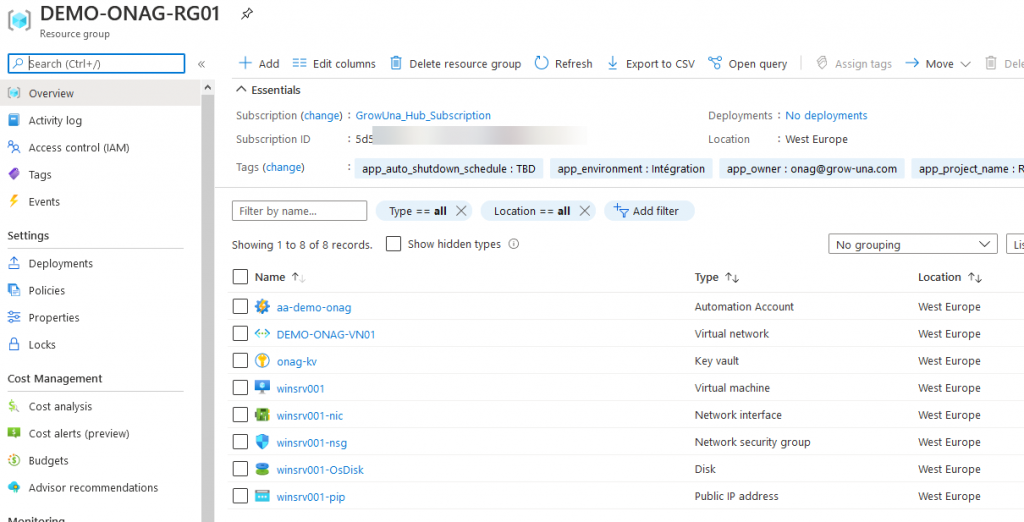
Create a Service Principal Name – SPN
- KV service: Key Vault Contributor
- VM service: Virtual Machine Contributor
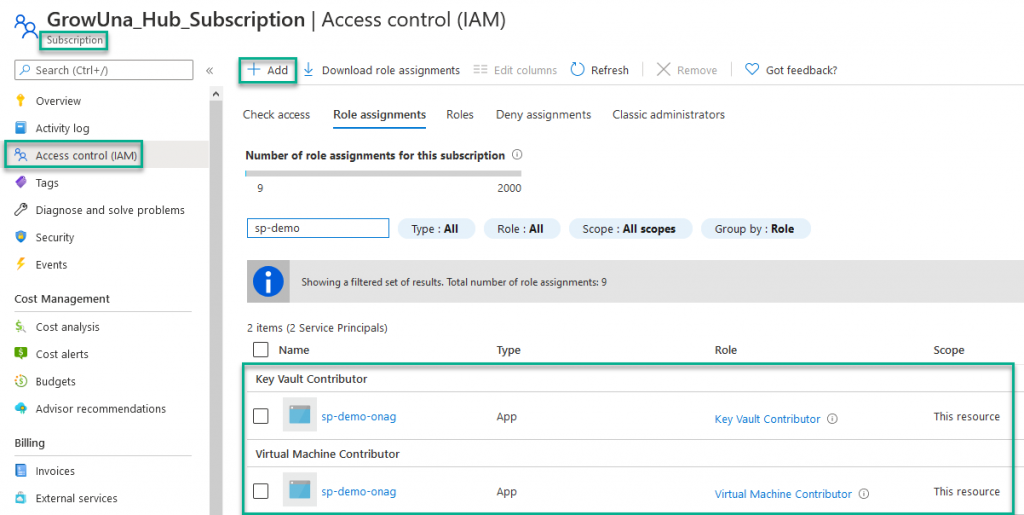
Access control has been given on the component, now we have to give access policies on secret permission on the KV to manage secret for the SPN created previously (included in the TF deployment):
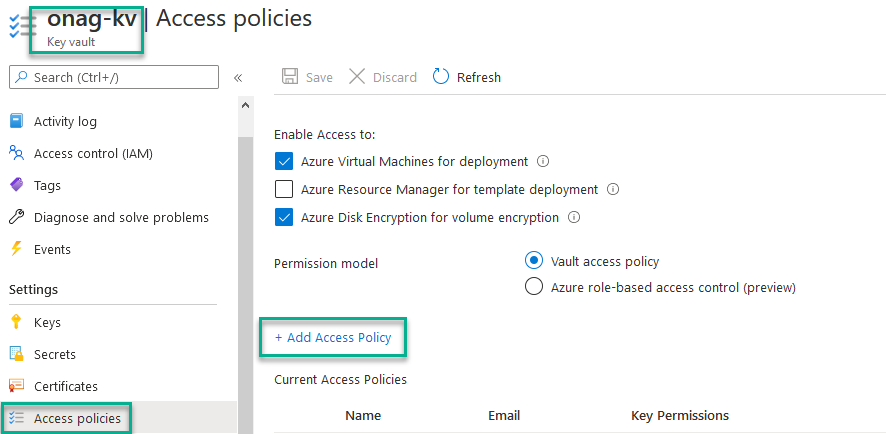
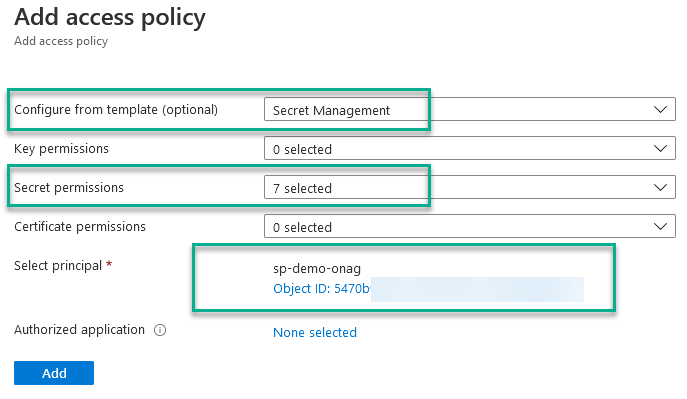
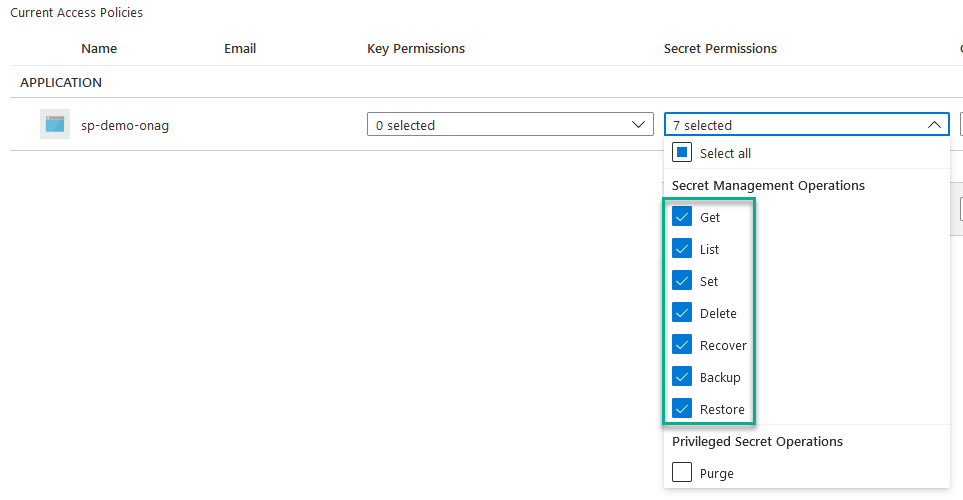
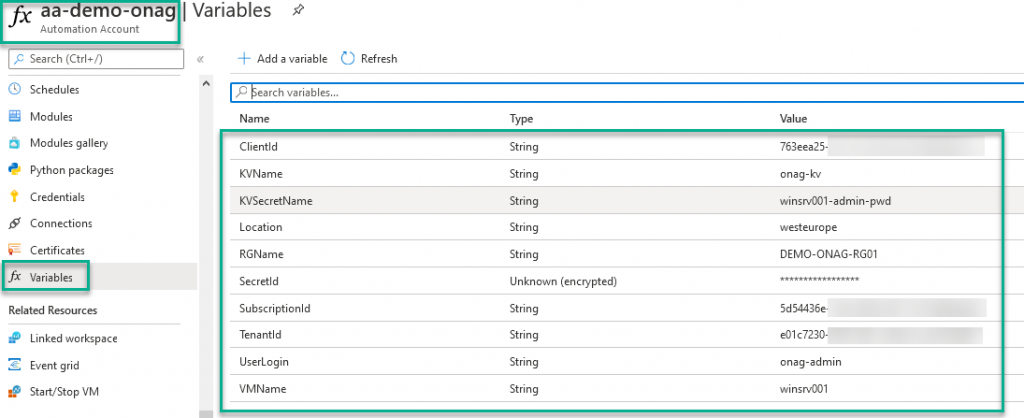
Define variables in AA
To avoid to expose critical data in scripts, variables are a secure way to do it.
The definition of the variables is included in the TF deployment, but if you want to do it manually, you can have a look to a previous post (in French) in which we describe the complete process.
The following variables must be defined to correctly execute the powershell runbook:
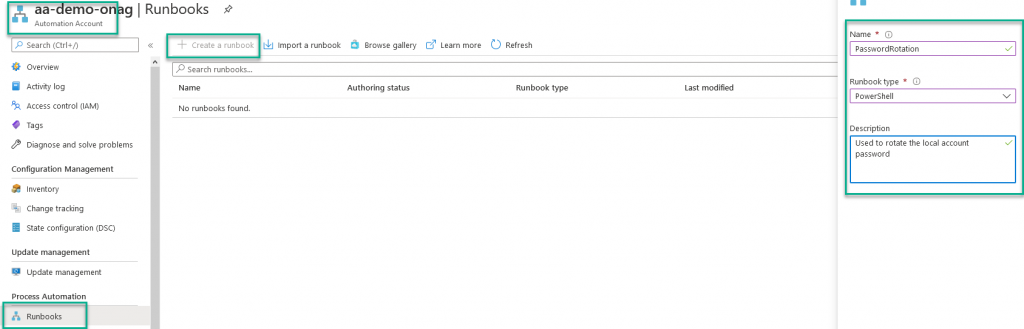
Create the Powershell runbook
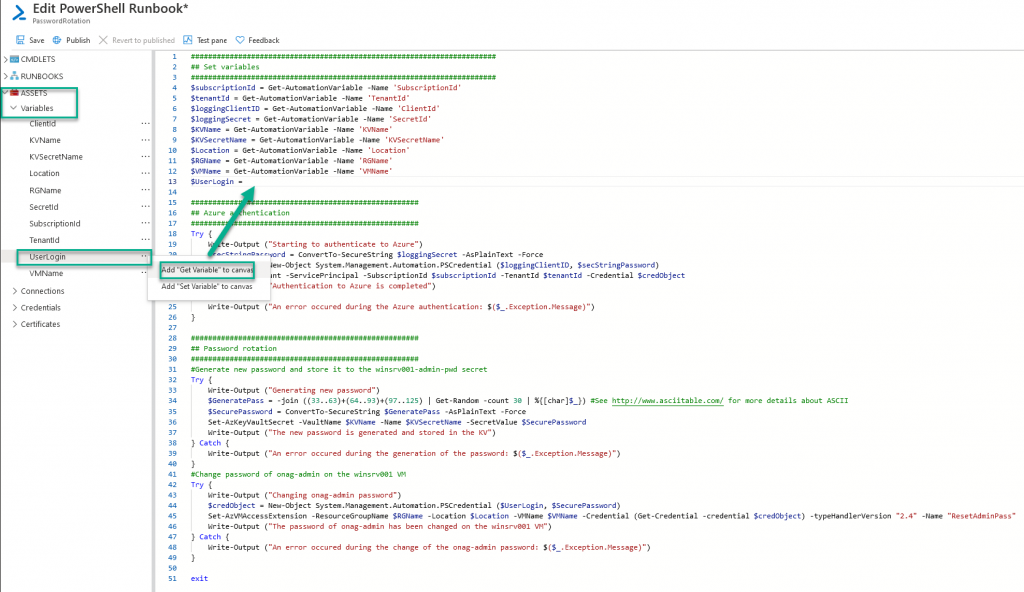
A little reminder, our goal, through a Powershell runbook, is to generate a new password that will be stored in KV, and used to change the local admin password on a VM.
Once the runbook is created, a new window opens, in which I copy the content of my script. All that remains is to declare the variables previously created. To do this, simply position yourself at the place where you want to define the value of your variable, click on the … and select Add « Get Variable » to canvas.
Repeat the operation for all the variables and finish by clicking on Save and Publish.
Warning: The Get variable and Set variable parameters cannot be used in a standard Powershell script but only in a powershell script in an Automation Account.
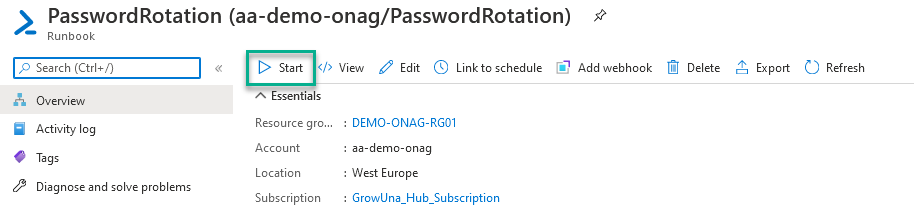
Runbook execution
After saving and publishing the script, you can start it to check if it works correctly.
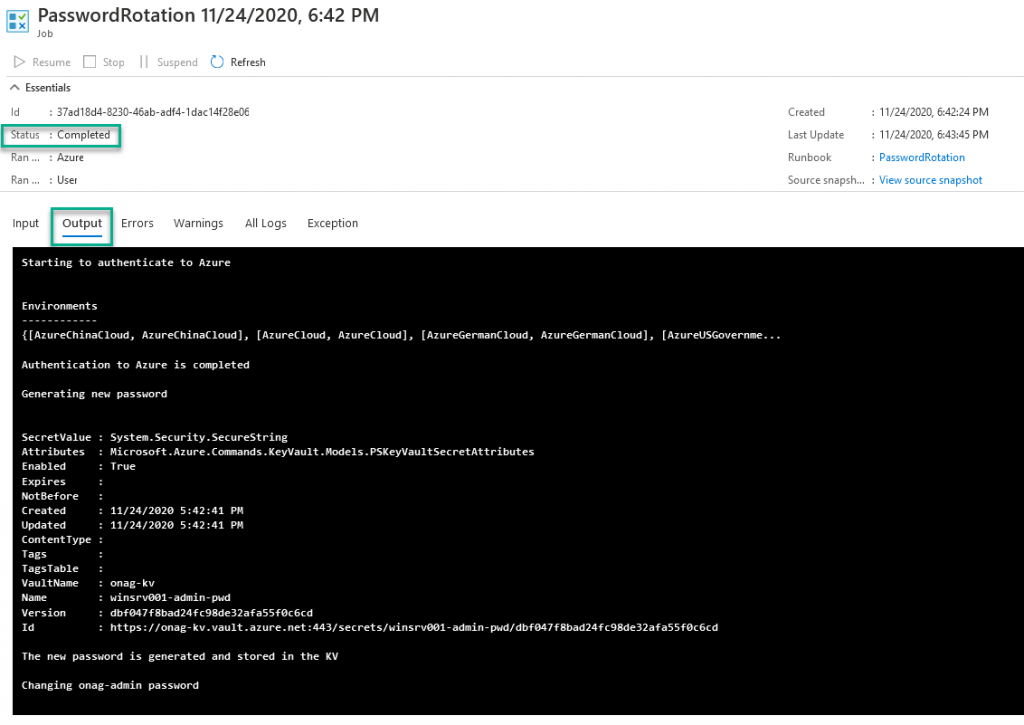
You can check the runbook execution with the Output tab
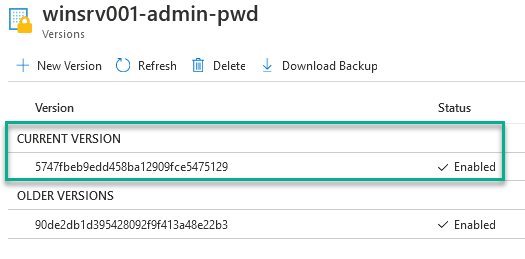
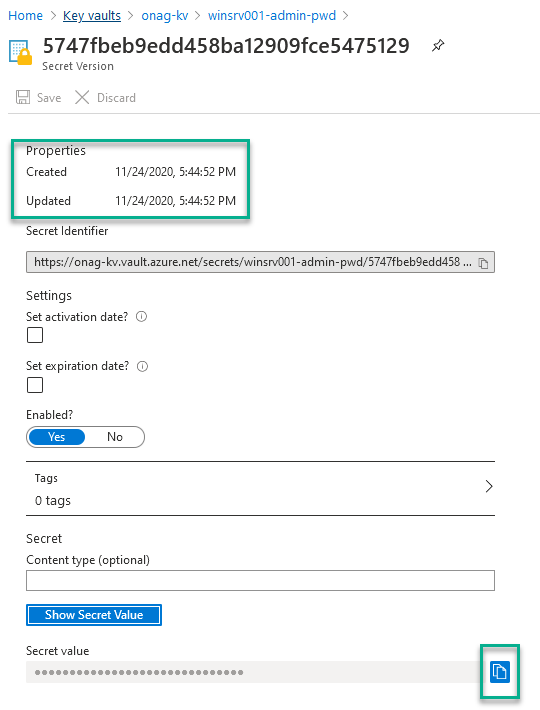
To validate that the runbook worked as expected, a new version of the secret should be exist on the KV, so you can try to connect on the VM with the combination of the Login and the new password
Conclusion
It is a simple, good and really cool solution at a lowest price.
Try & Explore:
- Combine your runbook with a schedule to plan the renewal at your own frequency
- Is it working with Linux VM ? Probably, but you have to prove it
- Try Hybrid runbook worker for VM deployed On-Premise or in other Cloud providers
- …



